Anonymization poses a challenge in cybersecurity as it aims to protect users’ identities while also obscuring criminals’ identities. This delicate balance between privacy and utility creates complexities in maintaining data security and privacy.
Anonymization is particularly challenging because it involves protecting users’ identities while obscuring criminal identification, a balance crucial for cybersecurity. The efficacy of network data anonymization is uncertain, making it challenging to determine the privacy implications and utility of published data.
Additionally, the complexity of modern technological advancements and their impact on data security complicates the management of large-scale data breaches. Moreover, ethical and practical concerns further complicate the sharing of proprietary operational data for legitimate research purposes. Balancing the values of openness, sound experimentation, and privacy is crucial when enabling data sharing with privacy controls.
Understanding Anonymization

Anonymization is a crucial concept in cybersecurity that involves the process of transforming personally identifiable information into a form that cannot be linked back to the original data subject. It plays a vital role in protecting user privacy and securing sensitive information, particularly in the context of data sharing and analysis. However, while anonymization offers significant benefits, it also presents notable challenges that need to be carefully addressed to ensure its effectiveness and reliability.
Balancing Privacy And Utility
An essential aspect of anonymization is the delicate balance between preserving the privacy of individuals and maintaining data utility for analysis and research purposes. Achieving this equilibrium is challenging as the level of anonymity must be sufficient to safeguard personal information, while still allowing meaningful insights to be derived from the data.
Challenges In Maintaining Anonymity
Several challenges are inherent in the maintenance of anonymity. The efficacy of anonymization techniques, uncertainties about privacy implications, and the complexity of modern technological advancements pose significant hurdles. Additionally, the ethical and practical concerns surrounding data sharing for legitimate research purposes further complicate the process of ensuring adequate anonymity.
In conclusion, understanding the intricacies of anonymization is essential for addressing the challenges it presents in cybersecurity. By acknowledging the need to balance privacy and utility, and by recognizing the specific difficulties associated with maintaining anonymity, organizations can implement more robust and effective strategies to protect sensitive data and uphold individual privacy.
Credit: www.mdpi.com
Risks And Pitfalls
In the realm of cybersecurity, anonymization poses several risks and pitfalls that organizations and researchers must be aware of. These challenges highlight the uncertainties surrounding its efficacy and the technological complexities involved.
Uncertainty Of Efficacy
One of the primary challenges of anonymization is the uncertainty surrounding its efficacy. While the purpose of anonymization is to protect users’ identities and obscure criminals’ identities, there is always a risk of potential identification breaches. The effectiveness of anonymization techniques is not foolproof and can be compromised due to various factors:
- De-identification attacks: Cybercriminals may deploy advanced methods to re-identify anonymized data and expose sensitive information. This possibility undermines the whole purpose of anonymization and puts users and organizations at risk.
- Data linkage: Anonymized data, when combined with other publicly available information, may inadvertently lead to the re-identification of individuals. This can occur through cross-referencing techniques or by exploiting patterns within the data.
These uncertainties surrounding the efficacy of anonymization necessitate continuous vigilance and a proactive approach to ensure data privacy and protection.
Technological Complexities
The technological complexities involved in implementing anonymization further contribute to the challenges of cybersecurity. Anonymizing data requires a comprehensive understanding of the underlying technology and a careful consideration of the following complexities:
- Privacy vs. utility: Striking the right balance between privacy and data utility is a delicate task. Anonymization techniques must ensure that data remains useful for research or analysis purposes while adequately protecting individuals’ identities.
- Appropriate definitions: Developing appropriate definitions for privacy and utility is crucial to guide the anonymization process. These definitions should align with legal and ethical requirements, adding another layer of complexity to the implementation.
- Impact of technological advancements: The constantly evolving technological landscape presents its share of challenges. Advances in technology can render existing anonymization techniques ineffective, making it imperative to stay updated and adapt to emerging technologies.
- Data breaches: Large-scale data breaches pose significant challenges to data security. Managing and securing vast amounts of data is complex, and any security lapse can render the anonymization efforts futile.
Addressing these technological complexities in a rapidly changing cybersecurity landscape requires continuous research, development, and adoption of robust anonymization strategies.
Ethical And Legal Implications

Anonymization in cybersecurity presents ethical and legal challenges as it aims to protect user privacy while obscuring criminal identities. Striking a balance between data privacy and utility is complex, requiring responsible practices and addressing the uncertainties associated with network data anonymization.
The growing impact of technological advancements further complicates data security management.
Data Privacy Concerns
Data privacy is a major concern when it comes to the anonymization of data in cybersecurity. With the use of advanced technologies, vast amounts of personal information are collected and stored by organizations. Customers and individuals often entrust their sensitive data to these organizations with the expectation that it will be kept private and secure.
However, anonymization introduces new challenges in maintaining data privacy. One of the main concerns is the possibility of re-identification. While anonymization methods are designed to remove personally identifiable information (PII) from data sets, there is still a risk that it can be reverse-engineered or combined with other information to identify individuals. This can lead to potential privacy breaches and the misuse of personal data. Another concern is the potential for data leakage.
Anonymized data sets may still contain some residual information that can be used to infer sensitive details about individuals. For example, a combination of demographic information and purchasing behavior could potentially reveal someone’s identity. This highlights the importance of ensuring that the anonymization process is thorough and effective in order to minimize the risk of data leakage.
Regulatory Compliance
Achieving compliance with relevant data protection regulations is another challenge that organizations face when it comes to anonymization in cybersecurity. Various laws and regulations, such as the General Data Protection Regulation (GDPR) in the European Union, outline specific requirements for the handling and anonymization of personal data. Organizations must ensure that their anonymization practices are in line with these regulations to avoid legal consequences.
They need to implement appropriate technical and organizational measures to protect personal data and demonstrate compliance with the principles of data protection. This includes the adoption of privacy by design and default principles, conducting data protection impact assessments, and ensuring the lawful processing of data. Failures in regulatory compliance can result in significant financial penalties and damage to an organization’s reputation.
Therefore, it is crucial for organizations to stay updated with the evolving regulations and ensure that they have robust anonymization processes in place to meet the requirements of these regulations. In conclusion, the ethical and legal implications of anonymization in cybersecurity are significant. Data privacy concerns and regulatory compliance are key aspects that organizations need to carefully consider and address. By prioritizing the protection of personal data and ensuring compliance with regulations, organizations can mitigate the risks associated with anonymization and enhance cybersecurity in a responsible and reliable manner.

Credit: www.mdpi.com
Anonymization Failures
Anonymization failures pose a challenge in cybersecurity due to the delicate balance required to protect user identities while obscuring criminal identities. Governments, for instance, cannot fully validate anonymization. The challenge lies in maintaining a balance between data privacy and utility, particularly when it comes to hiding criminal identification.
Limitations Of Data Anonymization
Data anonymization is a critical process used in cybersecurity to protect user privacy and ensure the confidentiality of sensitive information. However, it is not without its limitations. One of the primary challenges of data anonymization is maintaining a balance between privacy and data utility. When data is anonymized, it undergoes a transformation that removes personally identifiable information. However, this transformation can also come at the cost of losing valuable insights and analytics that can be derived from the data.
Anonymization techniques such as randomization or generalization can lead to a loss of granularity, making it challenging to obtain detailed insights from the data. This limitation affects various sectors, including healthcare, finance, and marketing, where detailed data insights are crucial for decision-making processes.
Another limitation of data anonymization is the risk of re-identification. Despite robust anonymization techniques, there is always a possibility that an individual can be re-identified based on other available data sources or by applying sophisticated de-anonymization techniques. This risk poses a significant challenge to ensuring the privacy and security of sensitive data.
Impact On Data Insight
The limitations of data anonymization directly impact the ability to gain valuable insights from the anonymized data. As mentioned earlier, the loss of granularity and detail due to anonymization can hinder organizations’ ability to gather meaningful and actionable insights. Detailed data insights are essential for businesses to make informed decisions, identify patterns, detect anomalies, and optimize operations.
However, when data is anonymized, it becomes challenging to conduct accurate analysis and extract valuable insights effectively. Moreover, the re-identification risk associated with anonymized data further compromises the usefulness of the insights derived from the data. If the anonymized data can be linked back to an individual, it raises significant privacy concerns and undermines the purpose of anonymization.
In conclusion, while data anonymization is crucial for ensuring privacy and security in the realm of cybersecurity, it presents challenges that impact data utility and insights. Organizations must carefully consider the limitations of anonymization techniques and develop robust strategies to mitigate the risks involved to strike a balance between privacy and data insights.
Importance Of Anonymization
Anonymization poses a challenge in cybersecurity as it strives to protect users’ identities while obscuring criminals’ identities. Achieving a delicate balance between privacy and utility is crucial, making anonymization an important aspect of data security.
Protection Of Identity
One of the key reasons why anonymization is a challenge in cybersecurity is its crucial role in protecting individual identities. In today’s digital age, where personal data is constantly being collected and shared, maintaining the privacy and confidentiality of users’ identities is of utmost importance. Anonymization techniques are employed to ensure that sensitive information, such as names, addresses, and financial details, cannot be traced back to specific individuals.
Cybersecurity Significance
The significance of anonymization in the realm of cybersecurity cannot be overstated. By effectively obscuring criminals’ identities, anonymization plays a vital role in preventing malicious activities and cyberattacks. It becomes increasingly challenging to combat cyber threats if criminals can operate under the cloak of anonymity. Anonymization helps law enforcement agencies and security professionals trace and apprehend cybercriminals, ensuring the safety and protection of individuals, organizations, and even nations.
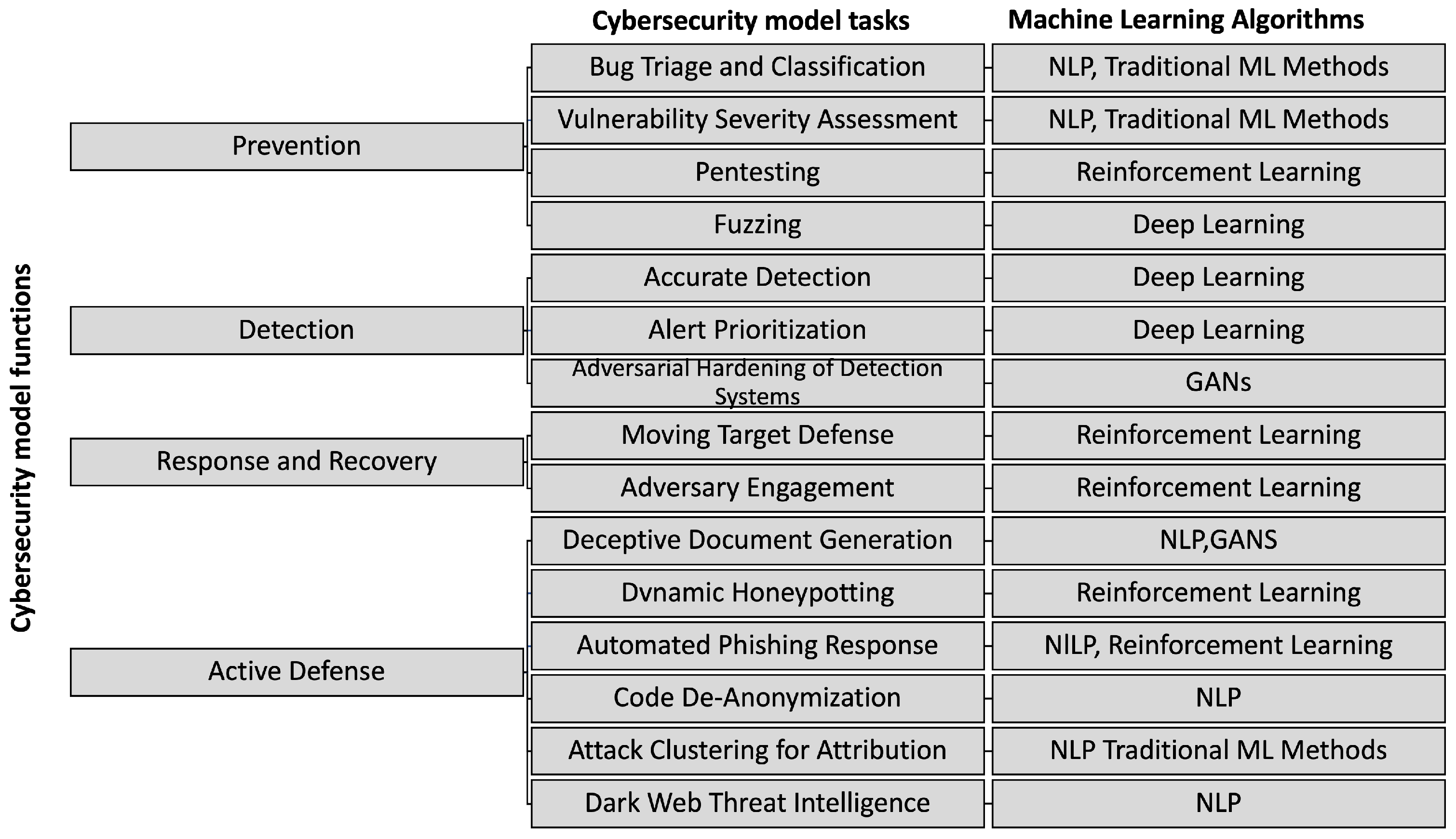
Credit: www.mdpi.com
Frequently Asked Questions Of Why Is Anonymization a Challenge in Cybersecurity
What Are The Problems With Data Anonymization?
The main problem with data anonymization is finding the right balance between privacy and utility. Anonymization protects users’ identities and obscures criminals’ identities, but it can also limit the value and insights derived from the data. Additionally, the efficacy of network data anonymization is uncertain, leaving researchers unsure about privacy implications and utility.
What Is Data Anonymization In Cyber Security?
Data anonymization in cybersecurity is the process of obscuring or removing personally identifiable information (PII) from a dataset to protect people’s privacy. It helps protect users’ identities and obscures criminals’ identities, striking a balance between privacy and utility. Governments often discourage anonymization.
What Is Anonymity In Cyber Security?
Anonymity in cyber security is the protection of user identity and the obscuring of criminals’ identities. It is a challenge because it requires a balance between privacy and the utility of data. Governments do not want anonymization as it hides criminal identification.
Why Is Anonymization Important?
Anonymization is important for protecting users’ identity and obscuring criminals’ identity in cybersecurity. It helps maintain a balance between privacy and data utility. It’s crucial for ensuring data privacy and preventing misuse by unauthorized individuals or entities.
Conclusion
In the realm of cybersecurity, anonymization poses a significant challenge. The delicate balance between privacy and utility of data is at the heart of this challenge. Anonymization aims to protect users’ identities, but in certain cases, it also hides criminal identification.
Establishing appropriate privacy measures while maintaining the necessary level of data utility is crucial. The complexities of modern technological advancements further complicate the management of large-scale data breaches. Finding the right balance between openness, privacy, and security remains a crucial task in the field of cybersecurity.



